Integrity Models
The UEFI Secure Boot chain can be applied to the Clark-Wilson integrity policy, developed in 1987. The Clark Wilson model includes the following concepts:
Data Item:
- Constrained Data Item (CDI)
- Unconstrained Data Item (UDI)
Procedure:
- Integrity Verification Procedure (IVP)
- Transformation Procedures (TPs)
Rule:
Certification Rule (CR) – integrity monitoring
C1: (Basic: IVP Certification) All IVPs must properly ensure that all CDIs are in a valid state.
C2: (Basic: Validity) All TPs must be certified to be valid. For each TP and each set of CDI that it may manipulate, the security officer must specify a “relation” of the form: (TP, {CDI}).
C3: (Separation of Duty Certification) The list of relation in E2 must be certified to meet the separation of duty requirement.
C4: (Journal Certification) All TPs must be certified to write to an append-only CDI (the log) all information necessary to permit the nature of the operation to be reconstructed.
C5: (Transformation Certification) Any TP that takes a UDI as an input value must be certified to perform only valid transformations, or no transformations, for any possible value of the UDI. The transformation should take the input from a UDI to a CDI, or the UDI is rejected.
Enforcement Rule (ER) – integrity preserving
E1: (Basic: Enforcement of Validity) The system must maintain the list of relation specified in C2, and must ensure that only TPs certified to run on a CDI manipulate that CDI.
E2: (Enforcement of Separation of Duty) The system must associate a user with each TP and set of CDIs in a list of relations of the form: (User, TP, {CDI}). It must ensure that only executions described in one of the relations are performed.
E3: (User Identity) The system must authenticate the identity of each user attempting to execute a TP.
E4: (Initiation) Only the agent permitted to certify entities may change the list of such entities associated with other entities, specifically the one associated with a TP. An agent that can certify an entity may not have any execute rights concerning that entity.
This model is based on the relationship between authenticated principal, program, and data items. The elements of this relationship are referred to as the “Clark-Wilson Triple” (User, TP, {CDI}). The Clark-Wilson model shows the rules required to meet the security properties of integrity: (from Blake).
Table 1-1: Clark-Wilson model
| Property | Description | Rule |
|---|---|---|
| Integrity | An assurance that CDIs can only be modified in constrained ways to produce valid CDIs. | C1, C2, C5, E1, E4 |
| Access Control | The ability to control access to resources. | C3, E2, E3 |
| Auditing | The ability to ascertain the changes made to CDIs and ensure that the system is in a valid state. | C1, C4 |
| Accountability | The ability to uniquely associate users with their actions. | E3. |
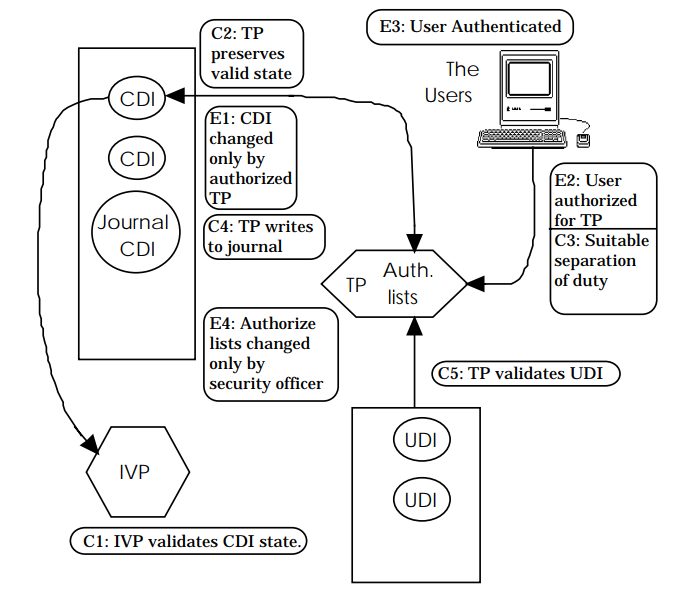
Figure 1-1: Clark-Wilson model, From Lee
Because the Clark-Wilson focuses on duty and transaction, it is more applicable to business and industry processes. Currently, some papers describe how to apply the Clark-Wilson integrity model to the existing system, such as Windows, Java or Trusted Computing Group (TCG) security.